As businesses increasingly adopt a ‘Bring Your Own Device’ (BYOD) culture, the accompanying security concerns have become more pressing. The convenience of BYOD comes with a significant downside: BYOD security risks.
69% of IT decision-makers in the US view BYOD as a positive trend, yet this enthusiasm is tempered by the reality of security concerns. It’s reported that 55% of professionals believe smartphones, a common BYOD item, are their most exposed endpoints in terms of security vulnerabilities.
| As David Stanton, Head of Cybersecurity/CISO, says, “Navigating BYOD challenges with a strong strategy ensures both security and productivity in a modern business setting.” |
This blog explores the top risks associated with BYOD and provides practical solutions to mitigate them, ensuring your business remains secure and efficient.
The Hidden Dangers of BYOD
The core appeal of BYOD lies in its flexibility and cost savings. Employees using their own devices for work-related tasks can boost productivity and satisfaction.
However, this flexibility opens the door to various BYOD risks and issues. One of the primary problems with BYOD is the blurring line between personal and professional use, which can lead to security risks of BYOD, including data breaches and leakage of sensitive information.
Carve Out a Digital IT Strategy that Captivates and Converts
Buchanan is the comprehensive solution you need.
Understanding The 5 Biggest BYOD Risks
1. Data Breach Vulnerability
BYOD devices often lack the advanced security measures found in corporate-issued hardware. This gap makes them vulnerable to cyber-attacks, increasing the risk of data breaches.
Cybercriminals target these devices because they know they can be the weakest link in a company’s security armor. Therefore, it’s crucial to address this gap to protect sensitive information.
2. Loss of Control Over Company Data
Allowing employees to use personal devices for work creates a complex situation in controlling access to company data.
Unlike corporate devices, where the company has complete control, personal devices present a challenge in monitoring and managing the use of sensitive information.
This lack of control can lead to unauthorized access or misuse of company data, potentially harming the organization’s interests and reputation.
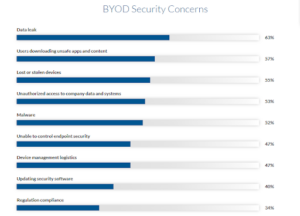
Source: FinancesOnline
3. Compliance Issues
Various laws and regulations govern data privacy and protection. BYOD introduces complexities in ensuring compliance with these regulations.
Personal devices might not always align with the required standards, creating legal risks. Non-compliance can lead to hefty fines and legal complications, making it essential for businesses to consider these aspects when adopting BYOD policies.
4. Network Security Threats
Personal devices frequently connect to different networks, including unsecured public Wi-Fi, posing significant BYOD security risks.
These networks are often not as secure as the corporate network, leaving the door open for malicious actors to exploit vulnerabilities. This can lead to unauthorized access to the corporate network and the potential leakage of sensitive data.
5. Risk of Lost or Stolen Devices
Personal devices are more susceptible to being lost or stolen, which can lead to security breaches. The portability of these devices means they are taken everywhere, increasing the risk of theft or loss.
When a device containing sensitive company information is lost or stolen, it poses a significant threat to the company’s data security.
How to Mitigate BYOD Risks
1. Implement Mobile Device Management (MDM) Solutions
MDM solutions are essential for monitoring and managing personal devices in a corporate setting. These solutions can enforce security policies, manage applications, and ensure that devices comply with company standards. They can remotely wipe data from lost or stolen devices, reducing the risk of data breaches.
2. Use Strong Authentication and Encryption
Implementing robust authentication methods and encryption is vital in protecting data on personal devices.
Two-factor authentication, strong passwords, and biometric scans add layers of security. Encryption ensures that even if the device falls into the wrong hands, the data remains inaccessible and secure.
3. Educate Employees
Employee education is critical in mitigating BYOD risks. Regular training sessions on security best practices for personal devices are essential.
Employees should understand the risks associated with BYOD and how their actions can prevent security incidents. This includes safe browsing habits, recognizing phishing attempts, and the importance of reporting lost or stolen devices immediately.
4. Establish a Comprehensive BYOD Policy
A well-crafted BYOD policy is the foundation of a secure BYOD environment. This policy should detail acceptable use, security requirements, and procedures for lost or stolen devices.
It should also cover aspects like data access rights, permissible applications, and device compliance standards.
5. Regular Security Audits and Updates
Conducting regular security audits is crucial to identify potential vulnerabilities in the BYOD setup. These audits should assess the effectiveness of current security measures and identify areas for improvement.
Additionally, ensuring that all devices receive the latest security updates and patches is critical in protecting against new threats and vulnerabilities.
More resources you might like: |
How Buchanan Technologies Can Assist in Mitigating BYOD Risks
In an era where Bring Your Own Device (BYOD) is becoming the norm, recognizing and addressing its risks is essential. Buchanan Technologies, a seasoned managed IT services provider, is your ally in navigating these challenges.
Our expertise lies in devising customized BYOD strategies and establishing strong security protocols to protect your business.
Discover Trusted Cybersecurity Services Near You: |
Instead of risking BYOD security, turn to Buchanan Technologies. With over 35 years of experience in the field, we’re equipped to offer practical, bespoke IT solutions that meet your specific needs.
Reach out to us for a free consultation today and benefit from our deep expertise and tailored IT solutions that fit your unique needs.










